Overview

Security has varying degrees of importance and endless applications: from idioglossia and encrypted message passing to padlock combinations and nuclear codes. At the heart of all these applications is information. Throughout history, people have developed new ways to share information with only the intended audience keeping those on the outside from learning what is shared. With the emergence of the Information Age and the constant improvements to performance and capabilities in computing, protecting information is more crucial than ever. It is estimated that 51% of the world’s population is connected to the Internet, making cyber security invaluable at both the consumer and industry sectors in addition to the government and military. The Information and Intelligent Security Lab has been established to investigate new methods of securing information, educating its members and enabling the implementation of emerging technologies to create more intelligent solutions.
Deep Reinforcement Learning for Vehicle-to-Everything (V2X)
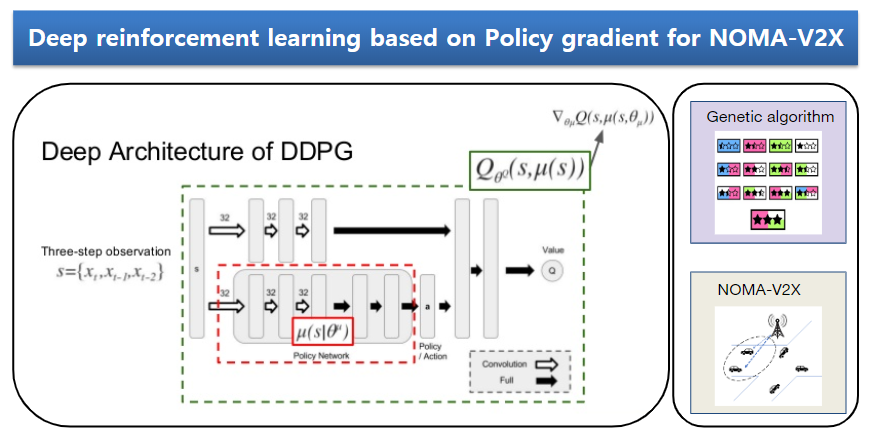
Deep learning technology is developing very quickly. One of the representative branches of advanced deep learning is Policy gradient based reinforcement learning. There are two neural networks: Actor and Critic. Critic is trained to predict a reward from the given states and actions. Then, Actor is trained to generate appropriate actions from the states to maximize the result of Critic. The key point of this methodology is that deep learning can derive unpredictable actions from human or simulations. The use of this deep learning methodology is unlimited. This project utilizes the method to solve a problem of Non Orthogonal Multiple Access in Vehicle to Everything (NOMA-V2X), one of the most challenging issues in 5G wireless communication.
Security and Privacy Issues in VANET
As the number of vehicles on the road and the size of the autonomous vehicle market sharply increase, the importance of Vehicular networks that can assist drivers is also significantly increasing. Vehicular ad hoc networks (VANETs) is a special research topic that lends itself to both the automotive industry as well as self-organizing wireless networking. In VANET, diverse traffic information is shared among vehicles such as accidents and congestions to provide enhanced driving experience. In this communication process, securing the privacy of vehicles as well as reliability of communication is imperative. This project aims to establish a secured communication network based on cryptographic methods and simulations to provide solutions for better driving environments.
Anomaly Detection
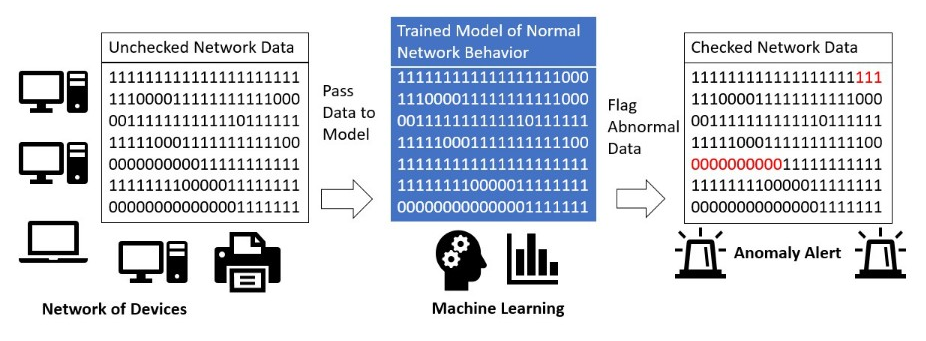
Network security is a concern for anyone that uses the Internet. Users want assurance that their information isn’t being stolen for nefarious purposes, and it has become very challenging to give users a guarantee that their network is secure, especially since many breaches happen due to user action. The aim of this project is to address the network security concern via a behavior analysis approach, which will assist security analysts better address network security issues and react quicker to various threats, e.g., zero-day attacks that include direct attacks on a network and newer attack methods such as the one caused by social engineering. This project considers and tests a broad spectrum of machine learning algorithms to train models on user behavior and to detect anomaly within a network.
Detecting Malware Employs a Cipher

As more users and devices connect to the internet (Cisco estimates some 480 million new users and 4.2 billion new devices by 2022), the number of potential victims grows. Malware or malicious software is a serious security risk as it hides itself as harmless software and to the average, layman user this may have serious consequences. As new security techniques develop, so too does the complexity of malware. Attackers have begun employing encryption to hide the malicious actions of their software. DarkComet (a tool that made international news when used during the conflicts in Syria), for example, encrypts its data using RC4. In a world where personal data is becoming increasingly digitized, we must continue to find new ways to thwart vulnerabilities.
Blockchain and Smart Contracts
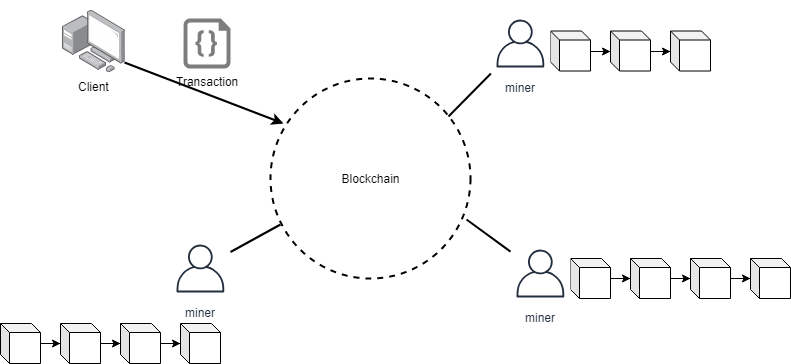
In 2008, with Bitcoin, Satoshi Nakamoto promoted the concept of Blockchain. Blockchain is a distributed ledger in which users can only append new transactions and read data from previous transactions. For new transactions to be added, they need to be processed and validated first; that process is handled through sets of instructions which are executed on top of the distributed ledger. These sets of instructions are commonly known as smart contracts. Blockchain and smart contracts offer possibilities to solve problems in different domains such as banking, healthcare, food industry, etc. The aim of our research is to look at previous solutions in different domains using blockchain and smart contracts and to devise new research directions.